Malicious actors continuously deploy new or improved techniques. Red teams must maintain an equally rapid pace of development of their tooling arsenal to remain effective at testing evolving defensive measure and preparing organizations for advanced threats. With the dedicated research and development efforts from the Outflank team, OST is constantly evolving, with additions of new, leading-edge tools unique to the market as well as regular enhancements to our existing tools.
In this quarterly release blog, we’ll summarize some of the latest updates we’ve made over the past few months.
EDR Tradecraft
Over the last few years we have clearly seen the big EDR names in the market up their game. Generally, we can say that they are doing a great job and that EDR-bypasses are becoming harder. However, EDRs can’t be expected to do magic, so there are still impressive, highly technical techniques that completely fly under the radar of even top tier EDRs.
An important change here is EDR bypass diversification: techniques that bypass all EDRs in one go are now increasingly less common. It is becoming more important for red teamers to know which exact technique to use (or not use) for a specific EDR. Up-to-date knowledge is important—particularly knowledge on how a specific EDR gets its data, how it works under the hood and where its blind spots and bypass opportunities lie. For OST we aimed on better equipping our customers with exactly that: knowledge.
Our experts spent months conducting deep technical research on the inner workings of major EDRs on the market. This resulted in significant updates to our documentation, detailing relevant details on the inner workings of EDRs, detailing generic bypass techniques, and major EDR specific techniques to use and techniques to not use. In our analysis of the behavioral detection methods of major EDRs, we were also able to both broaden our findings to provide strategies for general EDR evasion and create a methodology for when a more targeted approach is needed to avoid detection.
EDR Presets: An Opportunity for Community Sharing
We didn’t stop at EDR tradecraft knowledge in written form. We also wanted to make it more tangible and readily available in some of our tools. We started with what we call “EDR Presets” in our Payload Generator.
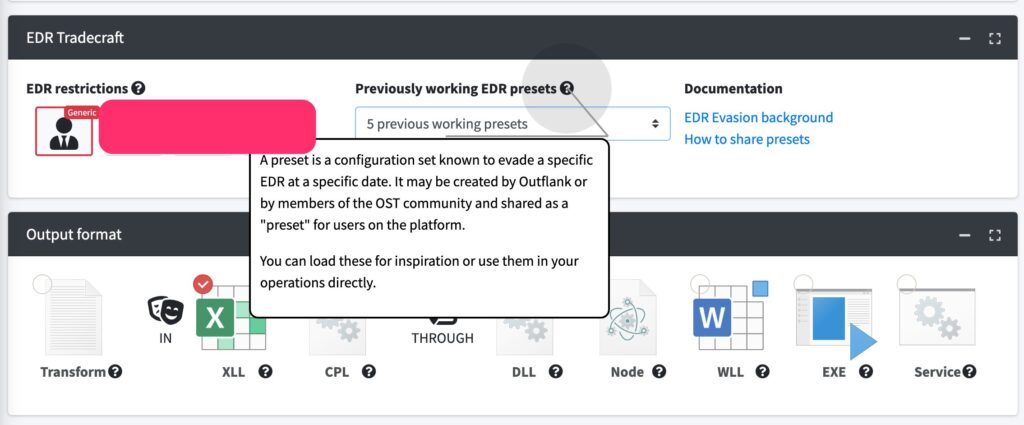
Payload Generator allows red team operators to easily create payloads with a wide range of decoy tricks, binary transformation options (such as prepending random shellcode), payload transformation options (such as encoding), encryption and compression, encryption possibilities, process creation techniques (such as Write Hook, KernelCallbackTable, Earlybird, in-process thread), as well as OPSEC tricks, guardrails and many more. The total set of option combinations easily surpasses a hundred, and it is critical to select the proper combination to bypass specific EDRs. EDR Presets are configuration sets of these 100+ settings in the Payload Generator.
Each EDR Preset has demonstrated the ability to evade detection by a certain EDR system at specific points in time. Though presets are incredibly useful and are a significant time saver for red team operators, they do have a limited shelf life. In order to maintain an up-to-date library of effective presets, we obviously perform ongoing lab testing. But as OST has a large community of active users, we decided to use that power of the community. We have implemented a secure way where OST users can contribute such presets they discovered during their engagements. This collaborative effort highlights the benefit of being a part of a strong user community, providing access to a collective pool of knowledge from which everyone can benefit.
Although this was simple in theory, the implementation took some time. Ultimately, it was very much worth the effort. EDR presets have quickly become a key feature that OST customers like, and we are proud to say that the community is actively using the sharing functionality.
PowerShell Tradecraft
PowerShell is often difficult to use in an OPSEC safe manner, as it can be challenging to sufficiently obfuscate. However, we have developed a new technique that, using some PowerShell trickery, allows for stealthy lateral movements. We’re not sharing too many details here on purpose because, as far as we know, this is not a publicly known technique.
Our tool can be used on its own, but we also wanted to integrate this in both Cobalt Strike and our own C2: Stage1 C2. The latter meant we needed to make Stage1 have support for PowerShell as well, so we went ahead and added this functionality.
New Microtools
While OST contains many tools with multi-functional capabilities, there are also times when a smaller tool is what’s called for. Two new tools we added this quarter were:
- WSManexec: This BOF to the internal C2 tool collection enables remote command execution via WSMan (the protocol used by WinRM) in a stealthy manner
- Keyper: This is a simple yet effective .NET keylogger that we created in response to user requests. It’s fully compatible with Stage1 and Cobalt Strike, but can also be useful as a standalone tool.
Additional Updates
- Stage1: The speed of SOCKS tunneling has been greatly accelerated.
- PetitPotam and PetitSystem: The PetitPotam and PetitSystem BOFs now have wider system support for Windows 10/11 desktops and servers. The RPC interface that was used by PetitPotam/PetitSystem to trigger EFS is no longer present on new Windows 11 clients. We researched alternative interfaces and made an update that supports both older and newer Windows versions. While this interface is not running by default, the tooling now triggers the EFS service to start first, after which the interface will be accessible.
- LAPSDump: This BOF now supports LAPS version 2.
The Continuing Growth of OST
Our formula for success with OST has consistently been grounded in three key pillars in order to support other red teams: tools, tradecraft, and community. Developing novel new tools that simplify and enhance engagements, offering educational opportunities that provide insightful new intel, and cultivating a solid community that facilitates connections and the exchange of experiences has enabled sustained growth and expansion. This proven formula also positions us to continue innovating, and we can’t wait to share more of what we’re working on.
If you’re interested in seeing all of the diverse offerings in OST, we recommend scheduling an expert led demo.