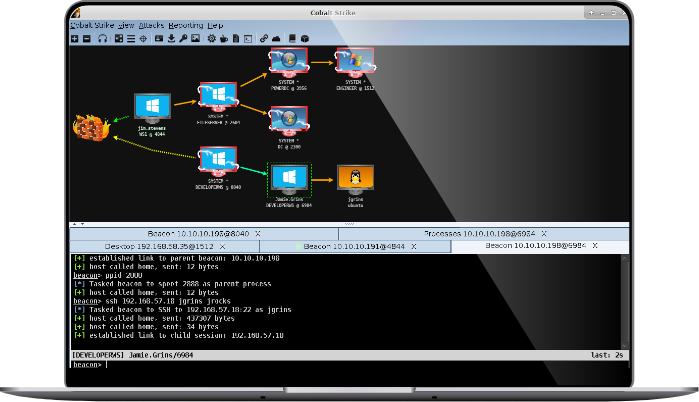
Cobalt Strike is a benchmark red teaming tool ideal for adversary simulations, particularly those with a focus on post-exploitation exercises. Using its adaptable C2 framework and signature advanced payload, Beacon, security professionals can replicate the tactics, techniques, and procedures of real-world attackers for accurate assessments of organizational defenses.
Features
Flexibility
Cobalt Strike’s malleable Command and Control (C2) framework can be easily extended with personalized tools and techniques. Tools published by Cobalt Strike’s user community are available in the Community Kit, a central repository with both tools and scripts.
Post-Exploitation
With Beacon, Cobalt Strike’s signature payload, users can replicate the behavior of an advanced adversary, quickly expanding their foothold.
Once deployed, Beacon can gather information, execute arbitrary commands, deploy additional payloads, and more. Further post-exploitation features can be added using Beacon Object Files (BOF), compiled C programs that can execute within a Beacon process.
Arsenal Kit
Operators can use Cobalt Strike’s collection of tools out of the box or tailor them to suit their engagements and support their goals. The Arsenal Kit currently includes:
- The Sleep Mask Kit – Hides Beacon in memory while it sleeps
- The Mutator Kit – Uses an LLVM mutator to break in-memory YARA scanning of sleep masks
- User-Defined Reflective Loaders – Custom reflective loaders that can bear individualized tradecraft
Covert Communication
Beacon provides several communication channels to reduce the risk of being identified:
- C2 Profiles – Change network indicators to either mask Beacon activity or simulate real-world ATPs
- HTTP, HTTPS, and DNS – Use Beacon to quietly egress networks
- Peer-to-peer Connections – Link Beacons to each other via TCP, or via named pipes using SMB
Collaboration
Cobalt Strike team servers enable red teams to communicate in real-time and coordinate efforts, sharing sessions, hosts, captured data, and downloaded files.
Payload Generation
Cobalt Strike can generate a wide variety of customizable payloads and also provides the option for users to create their own payloads that meet their specific needs.
Cobalt Strike Demo
Get a guided walkthrough of Cobalt Strike to see Cobalt Strike’s capabilities in action and learn how to navigate this powerful adversary simulation solution.
Cobalt Strike Interoperability
While Cobalt Strike excels when operating independently, its features can be further enhanced by working in tandem with other tools. The following tools can be used together throughout engagements using features like session passing and tunneling capabilities.
Outflank Security Tooling (OST)
This advanced offensive security toolset prioritizes evasion with tools that cover every step of the attack kill chain. OST integrates directly with Cobalt Strike through BOFs and reflective DLL loading techniques, providing an OPSEC safe way to efficiently perform highly technical and difficult post-exploitation tasks.
Core Impact
This automated penetration testing tool simplifies and centralizes exploiting vulnerabilities, moving laterally throughout an infrastructure, reporting, and re-testing. Core Impact and Cobalt Strike can unify engagements through session passing and tunneling capabilities and can also share resources, including Core Impact’s library of certified exploits and Cobalt Strike’s BOF API.
Cobalt Strike Pricing and Red Team Bundles
New Cobalt Strike licenses cost as low as $3,540, per user, for a one-year license when bundled with other proactive security solutions. For more information on pricing, fill out a quote request.
Red Team BundleCobalt Strike & Outflank Security Tooling (OST)Seamlessly integrate and extend the reach of these advanced red teaming solutions to run efficient adversary simulations designed to bypass modern defensive measures and detection tools with ease. Learn more |
Advanced Red Team BundleCobalt Strike, Core Impact, & OSTSafely evaluate infrastructures to create more resilient security strategies using a powerful combination of automated pen testing, a malleable post-exploitation framework, and a curated offensive security toolset. Learn more |